Reconnaissance is the first phase of an attack. In this phase attacker tries to gather information about the target person or organization before performing the actual attack. This phase is also known as footprint. Here the attacker mainly try to map structure, process and security expose of an organization. There are mainly two type of reconnaissance
- Passive reconnaissance
In this type of information gathering process attacker seeks to obtain information using public resources like website, news release, job posting etc.
2. Active Reconnaissance
In this type of information gathering process attacker directly interact with target using any means like visit as a visitor, telephone call, support assistant etc.
What are different methodology
Methodology used by attacker to perform active or passing reconnaissance.
1. using search engine like google, bing etc.
2. Using social media
3. Using tools like WHOIS
4. Using DNS footprinting.
5. Gathering information using social engineering.
6. Using public website and restricted website.
Actual tools used by Attackers
1. Google advance search:
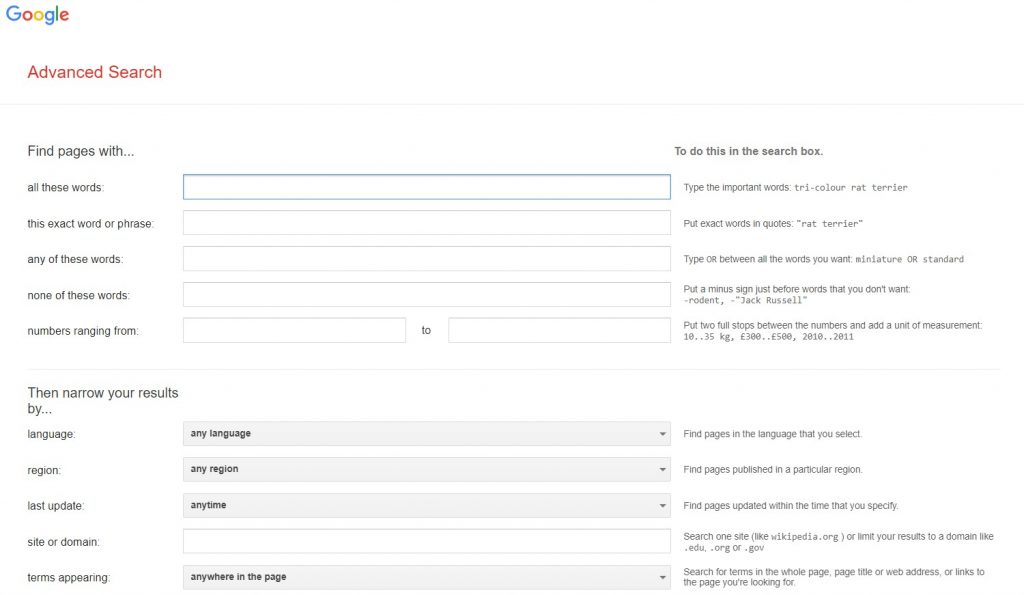
2. Google Hacking:
Google hacking, also named Google dorking, is a hacker technique that uses Google Search and other Google applications to find security holes in the configuration and computer code that websites are using.
For more details you can follow below link:
https://www.exploit-db.com/google-hacking-database
3. Facebook, Linkedin, twitter social Media site about people working the organization and their background and past history.
4. Website: platform use to build website, domain subdomains, department, hierarchy, top level management details. HTML source, cookie analysis.
5. Web spider tool like GSA email spider, web data extractor etc.
6. Extract past website history from archive.org.
7. Website-watcher to check for updates and changes on website.
