This is 4 hour chapter. This chapter will teach you network protocols and standards, interface and service, 7 layer of OSI model and its importance. TCP/Ip protocol suite and different networking hardware like NIC, Hub, router, repeater. 2.1. Protocols and Standards2.2. Interfaces and
Introduction to Computer Network which is of 3 teaching hours. Will teach you about following topics 1.1. Definition, merits, Demerits of computer network1.2. Network Models 1.2.1. PAN, LAN, Campus Area Network (CAN), MAN, Country Area Network(CAN*),
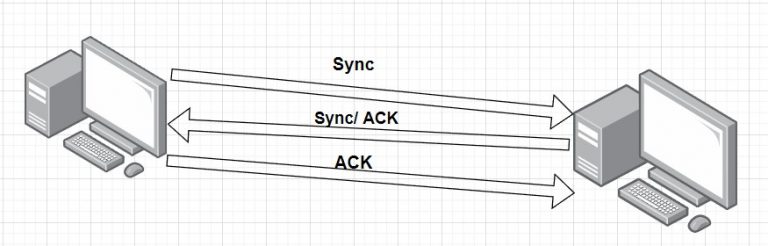
TCP also known as (Transmission Control Protocol ) is a layer 4 protocol (Transport Layer) of an OSI Model. TCP is a connection-oriented transport layer protocol that provides reliable full-duplex data transmission. TCP is part of the TCP/IP protocol stack. In a connection-oriented environment, a
Reconnaissance is the first phase of an attack. In this phase attacker tries to gather information about the target person or organization before performing the actual attack. This phase is also known as footprint. Here the attacker mainly try to map structure, process and security expose of an
Spear phishing Spear phishing is special type of phishing email or electronic communications scam targeted towards a specific individual, organization or business. These types of email are often intended to steal data for malicious purposes, cybercriminals may also intend to install malware on a
Linux Question Bank Solution This post share solution on most difficult and confusing questions of Bachelor of Computer Application (BCA) affiliated to Pokhara University on Linux subject. 2018 Fall 5 a) What do you mean by web server? Why are the needed? Explain. A web server is a computer that
Create User Account A user is an entity, in a Linux operating system, that can manipulate files and perform several other operations. Each user is assigned an ID that is unique for each user in the OS. Linux is multiuser OS where multiuser features enable many people to have accounts on a single
Reset/Recover Root Password Follow below procedure on how to break root password of CentOS 8. First, you need console access: Either at a keyboard and monitor locally, or via Virtual Machine remote console, you will need to see and interact with the bootloader. Reboot the machine: As soon as the
Monitoring System Performance: Lsof Command The lsof command is used in many Linux/Unix-like systems to display a list of all the open files and the processes. The open files included are disk files, network sockets, pipes, devices, and processes. One of the main reasons for using this command is
Monitoring System Performance: TOP Command Linux Top command is a performance monitoring program that is used frequently by many system administrators to monitor Linux performance and it is available under many Linux/Unix-like operating systems. The top command is used to display all the running
Checking System Space (Df and Du Command) 1. Df: Df command shows the amount of disk space used and available on Linux file systems.It display the amount of disk space used by the specified files and for each subdirectory.df, which stands for Disk Filesystem, is used to check disk space. It will
Add User to administrative Group (Sudoer) The sudo command stands for “Super User DO” and temporarily elevates the privileges of a regular user for administrative tasks. The sudo command in CentOS provides a workaround by allowing a user to elevate their privileges for a single task